how much time does a computer take to big calculations ?
Answers
Answer:
one billion (9 zeros) is being reached fast – 15 seconds. but to get to one trillion (12 zeros) – the difference is amazing – 4 hours and 10 minutes. Basically 1000 times more.
Explanation:
Related Questions
8. Show that x = xy + xy'
a) Using truth tables
b) Using Boolean identities
Answers
Answer:
B
Explanation:
Cause Show that x =Xy plus xy' is common = is Using Boolean Identify? tY me
Which technology is used for inventory planning
Answers
Answer:
WMS(Warehouse Mangement system )
Barcode System
LiFi Light fidelity Technology
What types of standards are developed by the Electronics Industries Alliance (EIA)?
Answers
Answer:
It comprises individual organisation that together have agreed on certain data transmissions standards such as EIA/TIA -232 formerly known as RS- 232
EIA 232D is an established standard by the Electronics Industry Association (EIA) that details the features of the electrical and physical connections between two devices. Each wire or pin required for serial communications has a name and an acronym.
Electronic Industry Association: What is it?The top producers of electronic components, as well as their approved distributors and manufacturer representatives, make up the Electronic Components Industry Association (ECIA). Promoting and enhancing the business climate for the authorised sale of electronic components is an objective shared by all ECIA members.
Economic and fiscal effect assessments, health impact assessments, risk assessments, social impact assessments, strategic impact assessments, and technology assessments are all examples of EIAs that can be performed.
An instrument used to evaluate the significant environmental impacts of a project or development proposal is the environmental impact assessment (EIA). EIAs ensure that project decision-makers consider the environment's likely effects as early as feasible and work to avoid, mitigate, or counteract those effects.
The Environmental Impact Assessment Regulations issued under the National Environmental Management Act of 1998 (EIA Regulations) (Act No. 107 of 1998).
To learn more About EIA, Refer:
https://brainly.com/question/28479703
#SPJ2
Write a program that reads a file name from the keyboard. The file contains integers, each on a separate line. The first line of the input file will contain the number of integers in the file. You then create a corresponding array and fill the array with integers from the remaining lines. If the input file does not exist, give an appropriate error message and terminate the program. After integers are stored in an array, your program should call the following methods in order, output the intermediate results and count statistics on screen, and at end output even integers and odd integers to two different files called even.out and odd.out.
Implement the following methods in the program:
* public static int[] inputData() – This method will ask user for a file name, create an array, and store the integers read from the file into the array. If input file does not exist, give an appropriate error message and terminate the program.
* public static void printArray(int[] array) – This method will display the content of the array on screen. Print 10 integers per line and use printf method to align columns of numbers.
public static void reverseArray(int[] array) – This method will reverse the elements of the array so that the 1st element becomes the last, the 2nd element becomes the 2nd to the last, and so on.
* public static int sum(int[] array) – This method should compute and return the sum of all elements in the array.
* public static double average(int[] array) – This method should compute and return the average of all elements in the array.
* public static int max(int[] array) – This method should find and return the largest value in the array.
* public static int min(int[] array) – This method should find and return the smallest value in the array.
* public static void ascendingSelectionSortArray(int[] array) – This method will use Selection Sort to sort (in ascending order) the elements of the array so that the 1st element becomes the smallest, the 2nd element becomes the 2nd smallest, and so on.
* public static void desendingBubbleSortArray(int[] array) – This method will Bubble Sort to sort (in descending order) the elements of the array so that the 1st element becomes the largest, the 2nd element becomes the 2nd largest, and so on.
* public static void outputData(int[] array) – This method will create two output files called even.out and odd.out. Scan through the entire array, if an element is even, print it to even.out. If it is odd, print the element to odd.out.
Answers
Answer:
Explanation:
import java.util.Scanner;
import java.io.*;
public class ArrayProcessing
{
public static void main(String[] args) throws IOException
{
Scanner kb = new Scanner(System.in);
String fileName;
System.out.print("Enter input filename: ");
fileName = kb.nextLine();
File file = new File(fileName);
if(!file.exists())
{
System.out.println("There is no input file called : " + fileName);
return;
}
int[] numbers = inputData(file);
printArray(numbers);
}
public static int[] inputData(File file) throws IOException
{
Scanner inputFile = new Scanner(file);
int index = 1;
int size = inputFile.nextInt();
int[] values = new int[size];
while(inputFile.hasNextInt() && index < values.length)
{
values[index] = inputFile.nextInt();
index++;
}
inputFile.close();
return values;
}
public static void printArray(int[] array)
{
int count = 1;
for (int ndx = 1; ndx < array.length; ndx++)
{
System.out.printf("%5.f\n", array[ndx]);
count++;
}
if(count == 10)
System.out.println("");
}
}
Declare a 4 x 5 list called N.
Using for loops, build a 2D list that is 4 x 5. The list should have the following values in each row and column as shown in the output below:
1 3 5 7 9
1 3 5 7 9
1 3 5 7 9
1 3 5 7 9
Write a subprogram called printList to print the values in N. This subprogram should take one parameter, a list, and print the values in the format shown in the output above.
Call the subprogram to print the current values in the list (pass the list N in the function call).
Use another set of for loops to replace the current values in list N so that they reflect the new output below. Call the subprogram again to print the current values in the list, again passing the list in the function call.
1 1 1 1 1
3 3 3 3 3
5 5 5 5 5
7 7 7 7 7
Answers
Answer:
# Define the list N
N = [[0 for j in range(5)] for i in range(4)]
# Populate the list with the initial values
for i in range(4):
for j in range(5):
N[i][j] = 2*j + 1
# Define the subprogram to print the list
def printList(lst):
for i in range(len(lst)):
for j in range(len(lst[i])):
print(lst[i][j], end=' ')
print()
# Print the initial values of the list
printList(N)
Output
1 3 5 7 9
1 3 5 7 9
1 3 5 7 9
1 3 5 7 9
--------------------------------------------------------------------
# Update the values of the list
for i in range(4):
for j in range(5):
N[i][j] = 2*i + 1
# Print the new values of the list
printList(N)
Output
1 1 1 1 1
3 3 3 3 3
5 5 5 5 5
7 7 7 7 7
Explanation:
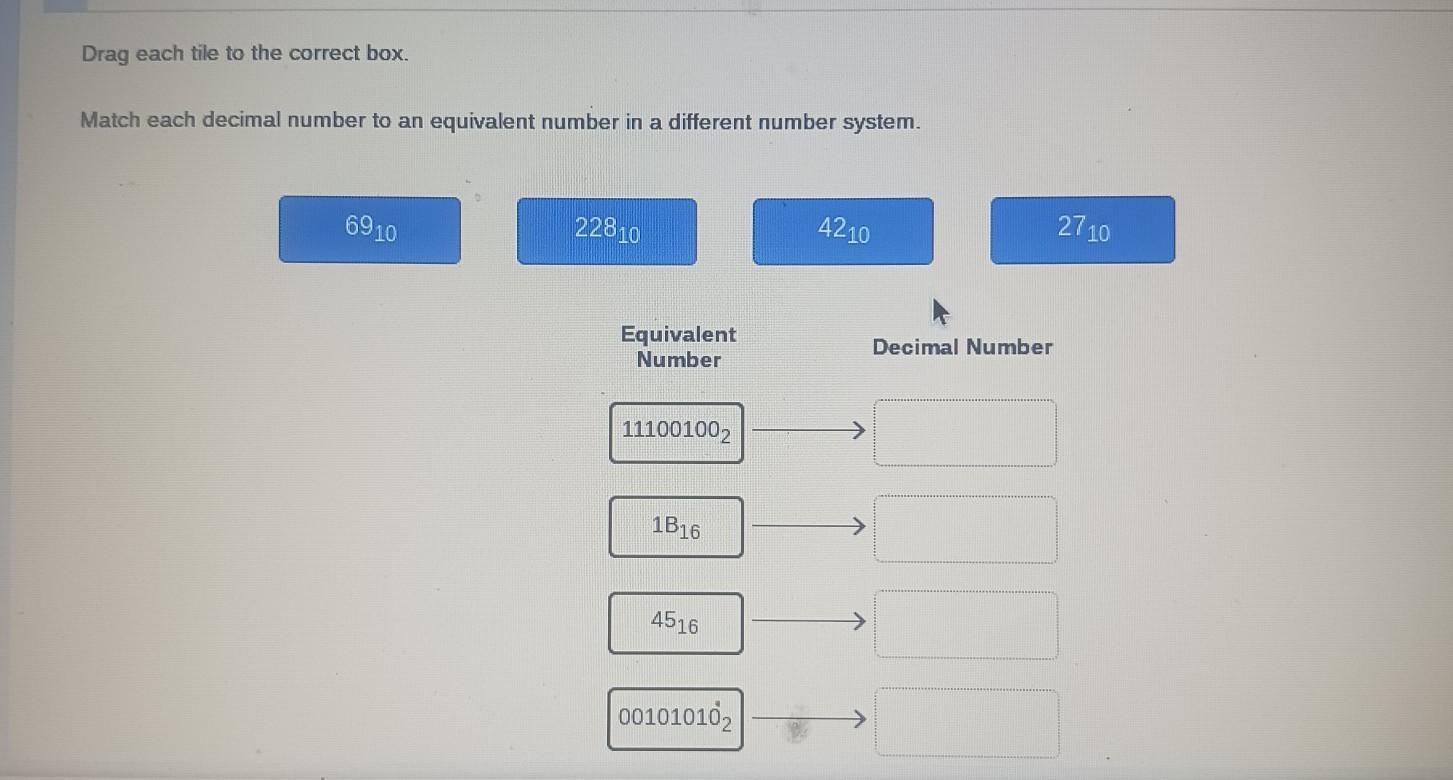
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
Answers
Explanation:
you can do that with calculator only

Most people have unexpected expenses at some time. Yes. No.
Answers
Answer:
Yes
Explanation:
I have no idea can someone answer

Answers
Answer:
FORTRAN and COBOL
Explanation:
LISP was developed around 1960 I believe and Microsoft for sure wasn't developed until at least 1970-1980. And searching for COBOL it was developed until 1959 so it could be that also.
If a file you are opening for appending does not exist, the operating system will detect the missing file and terminate the operation.
Answers
Answer:yes
Explanation:yes for a good night of love and love love miss
The following code will not display the results expected by the programmer. Can you find the error? Declare Real lowest, highest, average Display "Enter the lowest score." Input lowest Display "Enter the highest score." Input highest Set average = low + high / 2 Display "The average is ", average, "."
Answers
Based on the information given, the first error in the code is that the Variable name is lowest, NOT low, and Set average = low + high / 2.
How to find the error in the code.For Error 2: Variable name is highest, NOT high and Set average = low + high / 2
For Error 3 : Set average = low + high / 2. Thus, you will need to add the lowest and highest, then perform the division by 2
Set average = (lowest + highest) / 2 is the the correct statement.
Learn more about codes on:
https://brainly.com/question/25875879
Select the correct answer.
What type of depth of field did the photographer use for the image shown?
Ο Α.
a large depth of field
OB.
a small depth of field
O C.
a close depth of field
D.
a large as well as a small depth of field
OE.
no depth of field

Answers
Answer:
I think it's C. but not a 100%
Answer: It all ears to be a large depth of field
Explanation:
Elements in both the foreground and the background seem to be in focus, just as much as the bench. A small depth of field would have had the bench in sharp focus with the background and foreground out of focus.
Convert the following to CNF: S→SS|AB|B A→aAAa B→ bBb|bb|Ꜫ C→ CC|a D→ aC|bb
Answers
To convert the given grammar into Chomsky Normal Form (CNF), we need to rewrite the rules and ensure that each production has only two non-terminals or one terminal on the right-hand side. Here is the converted CNF grammar:
1. S → SS | AB | B
2. A → AA
3. A → a
4. B → bBb | bb | ε
5. C → CC | a
6. D → aC | bb
Explanation:
1. The production S → SS has been retained as it is.
2. The production A → aAAa has been split into A → AA and A → a.
3. The production B → bBb has been split into B → bB and B → b.
4. The production B → bb has been kept as it is.
5. The production B → ε (empty string) has been denoted as B → ε.
6. The production C → CC has been retained as it is.
7. The production C → a has been kept as it is.
8. The production D → aC has been kept as it is.
9. The production D → bb has been kept as it is.
In summary, the given grammar has been converted into Chomsky Normal Form (CNF), where each production has either two non-terminals or one terminal on the right-hand side. This form is useful in various parsing and analysis algorithms.
For more questions on parsing, click on:
https://brainly.com/question/13211785
#SPJ8
Answer:
Explanation:
To convert the given grammar to Chomsky Normal Form (CNF), we need to follow a few steps:
Step 1: Eliminate ε-productions (productions that derive the empty string).
Step 2: Eliminate unit productions (productions of the form A → B).
Step 3: Convert long productions (productions with more than two non-terminals) into multiple productions.
Step 4: Convert terminals in remaining productions to new non-terminals.
Step 5: Ensure all productions are in the form A → BC (binary productions).
Applying these steps to the given grammar:
Step 1: Eliminate ε-productions
The given grammar doesn't have any ε-productions.
Step 2: Eliminate unit productions
The given grammar doesn't have any unit productions.
Step 3: Convert long productions
S → SS (Remains the same)
S → AB
A → aAAa
B → bBb
B → bb
C → CC
C → a
D → aC
D → bb
Step 4: Convert terminals
No changes are needed in this step as all terminals are already in the grammar.
Step 5: Ensure binary productions
The given grammar already consists of binary productions.
The converted grammar in Chomsky Normal Form (CNF) is:
S → SS | AB
A → aAAa
B → bBb | bb
C → CC | a
D → aC | bb
Note: The original grammar didn't include the production rules for the non-terminals 'S', 'C', and 'D'. I assumed the missing production rules based on the provided information.
Write the steps to enter records in Datasheet view
Answers
Answer:
Overview of How to Add Records to a Table in Datasheet View in Access
You can easily add records to a table in datasheet view in Access. In datasheet view in Microsoft Access, there is a blank row at the bottom of the table. This row also contains an asterisk (*) in the row selector box at its left end. This is the “New Record” row. When you add records to a table in datasheet view in Access, each new record is added to the bottom of the table in the “New Record” row.
To add records to a table in datasheet view in Access, click into this row and enter the new record. The asterisk will then change to a picture of a “pencil” as you do this. That lets you know which record you are currently editing. Another new “New Record” row also appears below the row where you are entering data.
After opening a table in datasheet view, you can quickly move to the “New Record” row. To do this, click the “New Record” button at the right end of the “Record Navigation” button group in the lower-left corner of the datasheet view. It is the button with the [►*] face. Your cursor will then automatically enter into that row. You can then enter the new record’s data to add records to a table in datasheet view in Access.
A picture showing how to add records to a table in datasheet view in Access.
Instructions on How to Add Records to a Table in Datasheet View in Access
To add records to a table in datasheet view in Access, open the desired table in datasheet view.
Click the “New Record” button at the right end of the record navigation button group. This button group appears in the lower-left corner of the datasheet view. It is the button with the arrow and asterisk [►*] on its face.
Then enter the information into the fields in the “New Record” row. It is the bottommost row in the datasheet view that displays the asterisk [*] at the left end of the row.
When you have finished entering the new record, you can move down to enter the next new record into the new row that has appeared.
Close the table when you are finished adding
What kind of variable is measured using 2 different values
Answers
A variable that is measured using two different values can be classified as a categorical variable or a binary variable.
Depending on the nature of the values, a variable can be classified as:
1)Categorical Variable: If the two different values represent distinct categories or groups, the variable is considered categorical. In this case, the variable can take on only one of two possible values.
Examples include gender (male/female), presence/absence of a certain trait, yes/no responses, or any other classification with mutually exclusive categories.
2)Binary Variable: If the two different values represent two distinct outcomes or states, the variable can be classified as a binary variable. Binary variables are often used in statistics, machine learning, and hypothesis testing.
Examples include success/failure, true/false, 1/0, or positive/negative results.
It's important to note that the distinction between categorical and binary variables lies in the nature of the values and the underlying meaning they convey.
Categorical variables can have more than two categories, while binary variables specifically refer to variables with only two possible values.
For more questions on variable
https://brainly.com/question/28248724
#SPJ8
Which of these lines of code will generate a random number between 1 and 50? A. input("1-50") B. print("1-50") C. import random D. num = random.randint(1,50)
Answers
Answer:
D. num = random.randint(1,50)
Explanation:
The option given above will assign a random integer in the range of 1 through 50 to the variable number is: "number = random.randint(1, 50)"
What is a random integer in programming?This is a random sequence of integers that may be used to imitate things like shuffling a deck of cards or creating distinct behaviors every time a program runs. The RND function in BASIC generates random numbers. This yields a value between 0 and 1.
Random number creation is a technique that generates a series of numbers or symbols that cannot be realistically anticipated better than by random chance, generally using a random number generator (RNG).
Therefore, The option given above will assign a random integer in the range of 1 through 50 to the variable number is: "number = random.randint(1, 50)"
Learn more about random integers:
brainly.com/question/15247918
#SPJ3
3. What is a Trojan horse?
O A. Antivirus software for your computer
O B. Another name for a hacker
OC. A computer virus that can damage or delete files
O D. Software that eats cookies
Answers
What is the first phone ever made?
Answers
Answer:
the Telephone
Explanation:
Before the invention of electromagnetic telephones, mechanical acoustic devices existed for transmitting speech and music over a greater distance greater than that of normal direct speech. The earliest mechanical telephones were based on sound transmission through pipes or other physical media.The acoustic tin can telephone, or "lovers' phone", has been known for centuries. It connects two diaphragms with a taut string or wire, which transmits sound by mechanical vibrations from one to the other along the wire (and not by a modulated electric current). The classic example is the children's toy made by connecting the bottoms of two paper cups, metal cans, or plastic bottles with tautly held string.Some of the earliest known experiments were conducted by the British physicist and polymath Robert Hooke from 1664 to 1685. An acoustic string phone made in 1667 is attributed to him.For a few years in the late 1800s, acoustic telephones were marketed commercially as a competitor to the electrical telephone. When the Bell telephone patents expired and many new telephone manufacturers began competing, acoustic telephone makers quickly went out of business. Their maximum range was very limited. An example of one such company was the Pulsion Telephone Supply Company created by Lemuel Mellett in Massachusetts, which designed its version in 1888 and deployed it on railroad right-of-ways.Additionally, speaking tubes have long been common, especially within buildings and aboard ships, and they are still in use today. The telephone emerged from the making and successive improvements of the electrical telegraph. In 1804, Spanish polymath and scientist Francisco Salva Campillo constructed an electrochemical telegraph.The first working telegraph was built by the English inventor Francis Ronalds in 1816 and used static electricity. An electromagnetic telegraph was created by Baron Schilling in 1832. Carl Friedrich Gauss and Wilhelm Weber built another electromagnetic telegraph in 1833 in Göttingen.At the University of Gottingen, the two have been working together in the field of magnetism. They built the first telegraph to connect the observatory and the Institute of physics, which was able to send eight words per minute.
Part 1 Develop a 2- to 3-page table in Microsoft® Word that lists the roles and responsibilities of each of the following with respect to security. Use the following column headings: Title Role Responsibilities Use the following row headings: Chief Executive Officer (CEO) Chief Operations Officer (COO) Chief Financial Officer (CFO) Chief Information Officer (CIO) Chief Information Security Officer (CISO) Senior Security Manager Information Security Architect Information Security Engineer Information Security Auditor Information Security Analyst Security Technician/Specialist
Answers
The roles and responsibilities of the below-listed person with respect to security are:
Chief Executive Officer (CEO)- This person is responsible for making major corporate decisions, managing the overall operations and resources of a company
Chief Operations Officer (COO)- He is usually the second-in-command at the firm and can stand in when the CEO is unavailable.
Chief Financial Officer (CFO)- He is responsible for tracking cash flow and financial planning and analyzing the company's financial strengths
Chief Information Officer (CIO)- This person is in charge of information technology initiatives and strategy.
Chief Information Security Officer (CISO)- individual primarily responsible for the assessment, management, and implementation of information security in the organization.
Senior Security Manager Information- This person is in charge of managing the day-to-day operations of their organization's security department
Security Architect Information- This person is responsible for assessing the organization's systems for weaknesses. They conduct penetration tests
Security Engineer Information- This person is in charge of building digital security protocols, operating a cyber security system and maintaining an IT security infrastructure
Security Auditor Information- This person looks at the safety and effectiveness of computer systems and their security components,
Security Analyst- This person protects computer networks from cyber attacks, creates cybersecurity policies and practices f
Security Technician/Specialist- This person has the main duty to maintain and repair security-related concerns in a company.
Read more about Senior Security Manager here:
https://brainly.com/question/14467050
#SPJ1
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Fritz is a big fan of the racerville rockets. unfortunate;y, the team has been accused of cheating during their games. Fritz reads many articles and posts about this developing news story. His social media algorithms have "learned" that he's a fan of the team, so his feed doesnt show him any articles that argue the accusations are true. From this, Fritz decides his favorite team must be innocent of all cheating charges. Fritz is now in
A. a filter bubble
B. A third party
C. A subculture
D. an echo chamber
Answers
Option(D) is the correct answer. Fritz is now in an echo chamber.
Fritz's situation aligns with the concept of an echo chamber. An echo chamber refers to an environment, such as social media, where individuals are exposed to information and opinions that reinforce their existing beliefs and perspectives.
In this case, Fritz's social media algorithms have filtered out articles that present arguments in favor of the cheating accusations, creating an echo chamber that only confirms his preconceived notion of the team's innocence.
As a result, Fritz is insulated from diverse viewpoints and alternative perspectives, which can hinder critical thinking and a comprehensive understanding of the situation.
for similar questions on Fritz.
https://brainly.com/question/5100081
#SPJ8
Your friend Alicia says to you, “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I don’t think I’m going to do that.” How would you respond to Alicia? Explain.
Answers
Since my friend said “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I will respond to Alicia that it is very easy that it does not have to be hard and there are a lot of resume template that are online that can help her to create a task free resume.
What is a resume builder?A resume builder is seen as a form of online app or kind of software that helps to provides a lot of people with interactive forms as well as templates for creating a resume quickly and very easily.
There is the use of Zety Resume Maker as an example that helps to offers tips as well as suggestions to help you make each resume section fast.
Note that the Resume Builder often helps to formats your documents in an automatic way every time you make any change.
Learn more about resume template from
https://brainly.com/question/14218463
#SPJ1
Which of the following determines what specific features in a database system can be accessed by each user? Authorization
Answers
The key characteristics are as follows: 1) Offers backup for user-stored data, which the user can access whenever necessary. 2) Offers an interface for users to view the data.
Which of the following are features of database management systems?Reduced storage costs and space requirements, Minimum Redundancy and Duplication Data Organization, Database Customization, Data Retrieval, Query Language Use, Multi User Access, Data integrity is protected.One of the most essential aspects of the database approach is that the database system includes not only the database but also a comprehensive definition or description of the database structure and restrictions, sometimes referred to as database metadata.A database's data ought to include the following characteristics: Shared - A database's data are accessible by a variety of users and programmes. Data in a database have a persistent existence in the sense that they can survive processes that created them.To learn more about data refer to:
https://brainly.com/question/518894
#SPJ4
why do you think the design Process is important for designers to implement when creating a design?
Answers
The design process is important for designers to implement when creating a design for several reasons:
Systematic approachProblem-solvingCollaborationWhat is the design Process?Systematic approach: The design process provides a systematic and organized approach to creating a design. It involves steps such as research, planning, ideation, prototyping, testing, and refinement. Following a structured process helps designers to approach their work in a methodical manner, ensuring that all aspects of the design are thoroughly considered and addressed.
Problem-solving: The design process helps designers to approach design as a problem-solving activity. It encourages designers to identify the needs and requirements of the target audience or users, define the problem statement, and generate creative solutions to address the problem effectively. The process allows for experimentation, iteration, and refinement of design ideas until the best solution is achieved.
Collaboration: The design process often involves collaboration among team members or stakeholders. It provides a framework for designers to work together, share ideas, gather feedback, and make informed decisions. Collaboration fosters creativity, diversity of perspectives, and collective ownership of the design, leading to better outcomes.
Read more about design Process here:
https://brainly.com/question/411733
#SPJ1
What techniques overcome resistance and improve the credibility of a product? Check all that apply.
Including performance tests, polls, or awards
Listing names of satisfied users
Sending unwanted merchandise
Using a celebrity name without authorization
Answers
Answer: Including performance tests, polls, or awards.
Listing names of satisfied users
Explanation:
For every business, it is important to build ones credibility as this is vital on keeping ones customers and clients. A credible organization is trusted and respected.
The techniques that can be used to overcome resistance and improve the credibility of a product include having performance tests, polls, or awards and also listing the names of satisfied users.
Sending unwanted merchandise and also using a celebrity name without authorization is bad for one's business as it will have a negative effect on the business credibility.
Which expression has a value of ?
7/12
Answers
Answer: 7/12=0.5833 (etc)
Hope this helps!! brainlist plz?
If you have an array of 100 sorted elements, and you search for a value that does not exist in the array using a binary search, approximately how many comparisons will have to be done?
a)7
b)100
c)50
Answers
Answer:
50
Explanation:
as binary search will search the array by dividing it into two halves till it find the value.
In a balanced budget, the amount is the amount
Answers
In a balanced budget, the Income amount is same as the expense amount.
What is a balanced budget?A balanced budget is one in which the revenues match the expenditures. As a result, neither a fiscal deficit nor a fiscal surplus exist. In general, it is a budget that does not have a budget deficit but may have a budget surplus.
Planning a balanced budget assists governments in avoiding excessive spending and focuses cash on regions and services that are most in need.
Hence the above statement is correct.
Learn more about Budget:
https://brainly.com/question/15683430
#SPJ1
5.19 LAB: Countdown until matching digits
PYTHON: Write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.

Answers
Using the knowledge of computational language in python it is possible to write a code that write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.
Writting the code:n = int(input())
if 20 <= n <= 98:
while n % 11 != 0:
print(n)
n -= 1
print(n)
else:
print("Input must be 20-98")
See more about python at brainly.com/question/18502436
#SPJ1

metal cap is the negative terminal of an electric cell true or false please send me the answer please
Answers
what are reserved words with a programming language
Answers
This is a syntactic definition, and a reserved word may have no user-defined meaning. Often found in programming languages and macros, reserved words are terms or phrases appropriated for special use that may not be utilized in the creation of variable names. For example "print" is a reserved word because it is a function in many languages to show text on the screen