In one to two sentences, describe how to delete a file.
Answers
Answer:
To delete a file from your device right click the file.
Then in the special options pane that have appearred right when u right-clicked it, towards the bottom u will see option 'Delete', click it to delete the selected file
Related Questions
find four
reasons
Why must shutdown the system following the normal sequence
Answers
If you have a problem with a server and you want to bring the system down so that you could then reseat the card before restarting it, you can use this command, it will shut down the system in an orderly manner.
"init 0" command completely shuts down the system in an order manner
init is the first process to start when a computer boots up and keep running until the system ends. It is the root of all other processes.
İnit command is used in different runlevels, which extend from 0 through 6. "init 0" is used to halt the system, basically init 0
shuts down the system before safely turning power off.
stops system services and daemons.
terminates all running processes.
Unmounts all file systems.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
The software that allows multiple operating systems to run on a computer at the same time is called a(n) _____.
operating system manager
version
distribution
hypervisor
Answers
Answer:
hypervisor
Explanation:
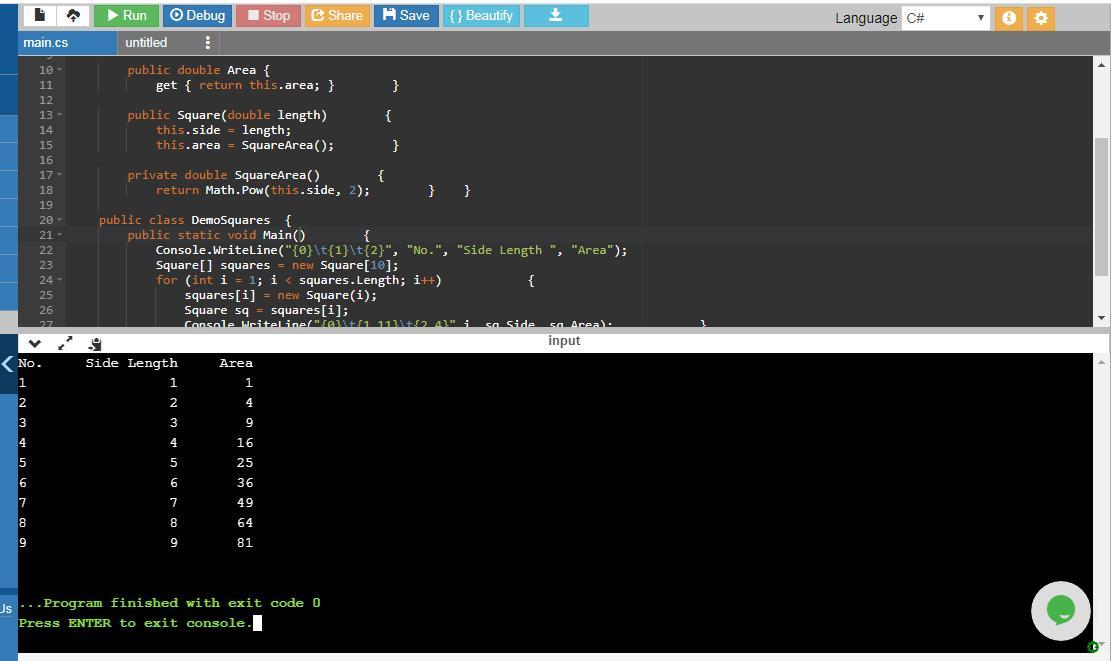
C# Create a program named DemoSquares that instantiates an array of 10 Square objects with sides that have values of 1 through 10 and that displays the values for each Square. The Square class contains fields for area and the length of a side, and a constructor that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method that computes the area field. Also include read-only properties to get a Square’s side and area.
Answers
Answer:
Here is the C# program.
using System; //namespace for organizing classes
public class Square //Square class
//private fields/variables side and area of Square class
{ private double side;
private double area;
//Side has read only property to get Square side
public double Side {
get { return this.side; }
}
//Area has read only property to get Square area
public double Area {
get { return this.area; } }
/*constructor Square(double length) that requires a parameter for the length of one side of a Square. The constructor assigns its parameter to the length of the Square’s side field and calls a private method SquareArea() that computes the area field */
public Square(double length) {
this.side = length;
this.area = SquareArea(); }
//method to calcuate area of a square
private double SquareArea() {
//Pow method is used to compute square the side i.e. side^2
return Math.Pow(this.side, 2); } }
public class DemoSquares {
public static void Main() { //start of main() function body
//displays the side and area on output screen
Console.WriteLine("{0}\t{1}\t{2}", "No.", "Side Length ", "Area");
//instantiates an array to input values 1 through 10 into Side
Square[] squares = new Square[10]; //squares is the instance
for (int i = 1; i < squares.Length; i++) {
//traverses through the squares array until the i exceeds the length of the //array
squares[i] = new Square(i);
//parameter is passed in the constructor
//new object is created as arrray is populated with null members
Square sq = squares[i];
/*display the no, side of square in area after setting the alignment to display the output in aligned way and with tab spaces between no side and area */
Console.WriteLine("{0}\t{1,11}\t{2,4}", i, sq.Side, sq.Area); }
//ReadKey method is used to make the program wait for a key press from //the keyboard
Console.ReadKey(); } }
Explanation:
The program is well explained in the comments mentioned with each statement of the program. The program simply has Square class which contains area and length of side as fields and a constructor Square which has length of one side of Square as parameter and assigns its parameter to length of Square side. The a private method SquareArea() is called that computes the area field. get methods are used to include read-only properties to get a Square’s side and area. The program along with its output is attached in the screenshot.

CONVERT to C# C# C# C# Just need C and Dpublic class Patterns { public static void main(String[]args) { char[][] arr=new char[10][10]; int starCount = 10; for(int i=0; i }}Need this code converted to "C# C# C# C# C# Just need C and D
Answers
Answer:
following are converted C# code:
using System; //import System
class Patterns //defining class Pattern
{
public static void Main() //defining main method
{
char[,] arr=new char[10,10];//defining char array
int starCount = 10;//defining integer variable starCount that holds value
int c=starCount;//defining integer variable c that holds starCount value
for(int i=0; i<c;i++,starCount--)//defining loop for column
{
for(int j=0; j<i; j++)//defining loop for rows
{
arr[i,j]='_'; //holds underscore value
}
for(int k=i; k<c; k++)//defining loop for rows
{
arr[i,k]='*';//holds asterik value
}
}
for(int a=0; a<c; a++)//defining loop for print column value
{
for(int b=0;b<c;b++) //defining loop for print row value
{
Console.Write(arr[a,b]);//print value
}
Console.WriteLine();//print space value
}
}
}
Output:
please find the attachment.
Explanation:
In the above given C# language code, firstly we import the package system, in the next step, Patters is declared, inside the class a char array "arr" and integer variable "starCount" is declared, that store integer value and the main method is declared.
In the method, for loop is defined, inside the loop, it stores "underscore and asterisk" value in the array.
Outside to loop another loop is defined, which uses the print method to print its value.
![CONVERT to C# C# C# C# Just need C and Dpublic class Patterns { public static void main(String[]args)](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/5GosCBN1gvcwR00ptWQW7vPZYcoK3L17.png)
Complete the code to generate a pseudo-random integer between 1 and 44, including the possibility of both 1 and
44.
>>> import secrets
>>> secret
Answers
Answer:
Explanation:
.randbelow(44) + 1
The code above uses the secrets module, which is a part of the Python standard library and uses a cryptographically strong random number generator. The randbelow() function generates a random integer below the number given as an argument. In this case, the argument is 44, which means that the function will generate a random integer between 0 and 43. To get a random integer between 1 and 44, we add 1 to the result of the function.
Sam is conducting research for a school project on the American Revolution. Which of the following kinds of software will help with research notes? music editing software word processing software presentation software spreadsheets
Answers
Answer:
Students analyze the techniques that make for good storytelling I think. :}
Explanation:
[] Hello ! []
Answer:
B. Word Processing Software
Explanation:
I hope it helped! :]
Write a program that defines the following two lists:
names = ['Alice', 'Bob', 'Cathy', 'Dan', 'Ed', 'Frank','Gary', 'Helen', 'Irene', 'Jack',
'Kelly', 'Larry']
ages = [20, 21, 18, 18, 19, 20, 20, 19, 19, 19, 22, 19]
These lists match up, so Alice’s age is 20, Bob’s age is 21, and so on. Write a program
that asks the user to input the number of the person to retrieve the corresponding
data from the lists. For example, if the user inputs 1, this means the first person
whose data is stored in index 0 of these lists. Then, your program should combine
the chosen person’s data from these two lists into a dictionary. Then, print the
created dictionary.
Hint: Recall that the function input can retrieve a keyboard input from a user. The
signature of this function is as follows:
userInputValue = input("Your message to the user")
N.B.: userInputValue is of type String
Answers
Answer: I used colab, or use your favorite ide
def names_ages_dict():
names = ['Alice', 'Bob', 'Cathy', 'Dan', 'Ed', 'Frank','Gary', 'Helen', 'Irene', 'Jack', 'Kelly', 'Larry']
ages = [20, 21, 18, 18, 19, 20, 20, 19, 19, 19, 22, 19]
# merging both lists
names_ages = [list(x) for x in zip(names, ages)]
index = []
# creating index
i = 0
while i < len(names):
index.append(i)
i += 1
# print("Resultant index is : " ,index)
my_dict = dict(zip(index, names_ages))
print('Input the index value:' )
userInputValue = int(input())
print(f'data at index {userInputValue} is, '+ 'Name: ' + str(my_dict[input1][0] + ' Age: ' + str(my_dict[input1][1])))
keys = []
values = []
keys.append(my_dict[input1][0])
values.append(my_dict[input1][1])
created_dict = dict(zip(keys, values))
print('The created dictionary is ' + str(created_dict))
names_ages_dict()
Explanation: create the function and call the function later

irving is running cable underground beside his driveway to power a light at his entrance .what type of cable is he most likely using?
A.MC
B.NNC
C.UFD
D.UF
Answers
Based on the given information, Irving is running cable underground beside his driveway to power a light at his entrance. The most likely type of cable he would use in this scenario is "D. UF" cable.
Why is the cable Irving is using a UF cable and its importanceUF stands for "Underground Feeder" cable, which is specifically designed for underground installations.
It is commonly used for outdoor applications, such as running power to lights, pumps, or other outdoor fixtures. UF cable is moisture-resistant and has insulation suitable for direct burial without the need for additional conduit or piping.
Read more about cables here:
https://brainly.com/question/13151594
#SPJ1
WORTH 75 POINTS!!
Which best describes the video encoding process?
converting analog video into digital video
filming a video at 30 frames per second
saving a digital video in a specific file format
watching a video while the file downloads
Answers
Answer:
To watch a digital video, you must use the codec that was used to encode the video file. Most videos are compressed.
Answer:
Why is compression important for video streaming?
to increase the number of frames per second so that motion appears smooth
to watch video without waiting for it to download(this one)
to improve image quality
to increase file size
Explanation:
Cryptography is an example of which part of the CIA triad?
Availability
Confidentiality
Integrity
Truthfulness
Answers
Cryptography is an example of ensuring Confidentiality in the CIA triad. (Option B)
How is this so?Cryptography is an essentialcomponent of ensuring Confidentiality within the CIA triad.
It involves the use of encryption techniques to protect sensitive information from unauthorized access.
By converting data into an unreadable format, cryptography ensures that only authorized individuals with the necessary decryption keys can access and understand the information,preserving its confidentiality and preventing unauthorized disclosure.
Learn more about Cryptography at:
https://brainly.com/question/88001
#SPJ1
Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
A hacker using information gathered from sniffing network traffic uses your banking credentials from a recent transaction to create nearly duplicate bank transfers but alters the target account to steal the funds. The attacker is reproducing traffic to re- create an event from previous transactions. This is an example of what type of attack?
A. Xmas attack
B. Smurf attack
C. DDoS attack
D. Replay attack
Answers
Answer: a replay attack, a replay attack is used so that the attacker can go sniff out the hash, and get whatever they are trying to get, then once it goes to the attacker it will go back to the original connection after replaying the hash
Hackers use packet sniffing attacks to intercept or steal potentially unprotected data from networks. A network-generated threat is a sniffing attack, also known as a packet sniffing assault. Thus, option D is correct.
What are the hacker using sniffing network?Snooping gives ethical hackers a lot of information about how a network functions and how its users behave, which can be used to improve a company's cybersecurity.
Sniffing can, however, be utilized by unscrupulous hackers to conduct catastrophic attacks against gullible targets.
A network sniffer can detect someone using excessive bandwidth at a college or commercial organization and hunt them down.
Therefore, replay attacks are employed so that the attacker can find the hash and obtain the desired object. Once the attacker has received the object, the replay attack causes the object to return to the original connection.
Learn more about sniffing network here:
https://brainly.com/question/10316246
#SPJ5
Using the Multiple-Alternative IFTHENELSE Control structure write the pseudocode to solve the following problem to prepare a contract labor report for heavy equipment operators: The input will contain the employee name, job performed, hours worked per day, and a code. Journeyman employees have a code of J, apprentices a code of A, and casual labor a code of C. The output consists of the employee name, job performed, hours worked, and calculated pay. Journeyman employees receive $20.00 per hour. Apprentices receive $15.00 per hour. Casual Labor receives $10.00 per hour.
Answers
Answer:
The pseudo-code to this question can be defined as follows:
Explanation:
START //start process
//set all the given value
SET Pay to 0 //use pay variable that sets a value 0
SET Journeyman_Pay_Rate to 20//use Journeyman_Pay_Rate variable to sets the value 20
SET Apprentices_Pay_Rate to 15//use Apprentices_Pay_Rate variable to sets the value 15
SET Casual_Pay_Rate to 10//use Casual_Pay_Rate variable to set the value 10
READ name//input value
READ job//input value
READ hours//input value
READ code//input value
IF code is 'J' THEN//use if to check code is 'j'
COMPUTE pay AS hours * JOURNEYMAN_PAY_RATE//calculate the value
IF code is 'A' THEN//use if to check code is 'A'
COMPUTE pay AS hours * APPRENTICES_PAY_RATE//calculate the value
IF code is 'C' THEN//use if to check code is 'C'
COMPUTE pay AS hours * CASUAL_PAY_RATE//calculate the value
END//end conditions
PRINT name//print value
PRINT job//print value
PRINT code//print value
PRINT Pay//print value
END//end process
Elaborate me rale OF ICT in Education.
Answers
Information and Communication Technology (ICT) plays a crucial role in transforming education by enhancing teaching and learning processes,
Elaborations on the role of ICT in education:Access to Information and Resources: ICT provides students and educators with access to a vast amount of information and educational resources. Through the internet, digital libraries, and online databases, learners can access a wide range of educational materials, research articles, e-books, videos, and interactive content. This enables them to explore diverse topics, conduct research, and stay updated with the latest information in their respective fields.
Enhancing Teaching and Learning: ICT tools and technologies enhance teaching and learning experiences. Multimedia presentations, educational software, simulations, and virtual reality applications engage students and make learning interactive and dynamic. Online platforms and learning management systems provide educators with the ability to deliver course materials, assignments, and assessments in a structured and organized manner. This fosters active learning, critical thinking, and problem-solving skills among students.
Learn more about ICT at
https://brainly.com/question/13724249
#SPJ1
complete question
Elaborate on the role OF ICT in Education
In Coral Code Language - A half-life is the amount of time it takes for a substance or entity to fall to half its original value. Caffeine has a half-life of about 6 hours in humans. Given the caffeine amount (in mg) as input, output the caffeine level after 6, 12, and 18 hours.
Ex: If the input is 100, the output is:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
Note: A cup of coffee has about 100 mg. A soda has about 40 mg. An "energy" drink (a misnomer) has between 100 mg and 200 mg.
Answers
To calculate the caffeine level after 6, 12, and 18 hours using the half-life of 6 hours, you can use the formula:
Caffeine level = Initial caffeine amount * (0.5 ^ (time elapsed / half-life))
Here's the Coral Code to calculate the caffeine level:
function calculateCaffeineLevel(initialCaffeineAmount) {
const halfLife = 6; // Half-life of caffeine in hours
const levelAfter6Hours = initialCaffeineAmount * Math.pow(0.5, 6 / halfLife);
const levelAfter12Hours = initialCaffeineAmount * Math.pow(0.5, 12 / halfLife);
const levelAfter18Hours = initialCaffeineAmount * Math.pow(0.5, 18/ halfLife);
return {
'After 6 hours': levelAfter6Hours.toFixed(1),
'After 12 hours': levelAfter12Hours.toFixed(1),
'After 18 hours': levelAfter18Hours.toFixed(1)
};
}
// Example usage:
const initialCaffeineAmount = 100;
const caffeineLevels = calculateCaffeineLevel(initialCaffeineAmount);
console.log('After 6 hours:', caffeineLevels['After 6 hours'], 'mg');
console.log('After 12 hours:', caffeineLevels['After 12 hours'], 'mg');
console.log('After 18 hours:', caffeineLevels['After 18 hours'], 'mg');
When you run this code with an initial caffeine amount of 100 mg, it will output the caffeine levels after 6, 12, and 18 hours:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
You can replace the initialCaffeineAmount variable with any other value to calculate the caffeine levels for different initial amounts.
for similar questions on Coral Code Language.
https://brainly.com/question/31161819
#SPJ8
4. Interaction between seller and buyer is called___.
A. Demanding
B. Marketing
C. Transactions
D. Oppurtunity
Answers
Answer:
C. Transactions.
Explanation:
A transaction can be defined as a business process which typically involves the interchange of goods, financial assets, services and money between a seller and a buyer.
This ultimately implies that, any interaction between a seller and a buyer is called transactions.
For example, when a buyer (consumer) pays $5000 to purchase a brand new automobile from XYZ automobile and retail stores, this is referred to as a transaction.
Hence, a transaction is considered to have happened when it's measurable in terms of an amount of money (price) set by the seller.
Price can be defined as the amount of money that is required to be paid by a buyer (customer) to a seller (producer) in order to acquire goods and services. Thus, it refers to the amount of money a customer or consumer buying goods and services are willing to pay for the goods and services being offered. Also, the price of goods and services are primarily being set by the seller or service provider.
You are given a decimal number to convert into binary. Press the buttons to
change their values so that the row represents the decimal number on the left.
When a 1 is used, we consider the value to be ON. When a 0 is used, we consider
the value to be OFF.
128
90
69
93
76
47
12
66
122
70
103
Answers
128: 10000000
90: 01011010
69: 01000101
93: 01011101
76: 01001100
47: 00101111
12: 00001100
66: 01000010
122: 01111010
70: 01000110
103: 01100111
What kind of block do you need to check whether a sprite is touching another sprite?
A. forever block
B. A repeat 10 block
C. An if block
D.An event block
Answers
A event block i know this im i have been in technology for 5 months
If an artist would like a drawing to be freely available everyone, make it
Answers
Answer:
he first would draw it with paint and that it I want to say
Is that a question or you are saying?
Explanation:
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
6. What are the arguments, pros and cons, for Python's use of indentation to specify compound statements in control statements
Answers
Answer:
\(beinggreat78~here~to~help.\)
In some cases, one con is that it can be hard to keep track of your identation when coding long lines or blocks. The pro is that you may need to learn, which is not a bad thing. Learning is good.
What is the original
name for Pendrive
Answers
Answer:
The first flash drives had 8 megabytes of storage. Each year, larger flash drives will become available. In April 2012, 256 gigabyte flash drives were introduced to the market. Other common names for a flash drive include pendrive, thumbdrive or simply USB.
Explanation:
In this exercise, we examine how pipelining affects the clock cycle time of the processor. Problems in this exercise assume that individual stages of the datapath have the following latencies:
IF ID EX MEM WB
250ps 350ps 150ps 300ps 200ps
Also, assume that instructions executed by the processor are broken down as follows:
alu beq sw sw
45% 20% 20% 15%
1. What is the clock cycle time in a pipelined and non-pipelined processor?
2. What is the total latency of an LW instruction in a pipelined and non-pipelined processor?
3. If we can split one stage of the pipelined datapath into two new stages, each with half the latency of the original stage, which stage would you split and what is the new clock cycle time of the processor?
4. Assuming there was are no stalls or hazards, what is the utilization of the data memory?
5. Assuming there are no stalls or hazards, what is the utilization of the write-register port of the "Registers" unit?
6. Instead of a single-cycle organization, we can use a multi-cycle organization where each instruction takes multiple cycles but one instruction finishes before another is fetched. In this organization, an instruction only goes through stages it actually needs (e.g., ST only takes 4 cycles because it does not need the WB stage). Compare clock cycle times and execution times with single-cycle, multi-cycle, and pipelined organization
Answers
The clock cycle time in a pipelined and non-pipelined processor will be 350ps and 1250ps respectively.
1. The clock cycle time in a pipelined processor will be the slowest instruction decode which is 350ps. The clock cycle time in a non-pipelined processor will be:
= 250 + 350 + 150 + 300 + 200
= 1250ps
2. The total latency of an LW instruction in a pipelined processor will be:
= 5 × 350 = 1750ps.
The total latency of an LW instruction in a non-pipelined processor will be:
= 250 + 350 + 150 + 300 + 200
= 1250ps
3. Based on the information asked, the stage to be split will be the cycle time. Now, the new cycle time will be based on the longest stage which will be 300ps.
4. It should be noted that the store and load instruction is used for the utilization of memory. The load instruction is 20% of the time while the store instruction is 15% of the time. Therefore, the utilization of data memory will be:
= 20% + 15% = 35%
5. The utilization of the write-register port of the "Registers" unit will be:
= 20% + 45% = 65%
6. The multi cycle execution time will be:
= (5 × 20%) + [4 × (45% + 20% + 15%)]
= (5 × 0.2) + (4 × 0.8)
= 1 + 3.2
= 4.2
The single cycle execution time will be:
= Cycle time non-pipeline / Cycle time pipeline
= 1250/350
= 3.5
Read related link on:
https://brainly.com/question/25231696
3-2: Using Libraries: The C++ language includes functions organized into a series of libraries. Your text documents some of these libraries in Appendix F. Part A Refer to the functions contained in the cmath (math.h) library. Identify a function that will find the absolute value of a number. Indicate how many pieces of data must be passed to the function. Indicate, what (if anything) will be returned by the function. Demonstrate the appropriate use of the function in a short code fragment. Part B Refer to the functions contained in the cmath (math.h) library. Identify a function that will determine the value of x raised to the y power. Indicate how many pieces of data must be passed to the function. Indicate, what (if anything) will be returned by the function. Demonstrate the appropriate use of the function in a short code fragment.
Answers
The cmath (math.h) library's abs function can be used to determine a number's absolute value (). The integer whose absolute value has to be determined is the only piece of data that must be supplied to the function.
Is there an absolute value for cmath?In C++, the abs() method returns the argument's absolute value. It is specified in the header file for cmath. In mathematics, abs(num) equals |num|.
cmath> is included.
Including the iostream tag.
-10; int abs num; int main(); int num; The absolute value of num is "" abs num std::endl; return 0; "" std::abs(num); std::cout;
To know more about data visit:-
https://brainly.com/question/13650923
#SPJ1
What factors do network consultants consider when determining the network needs of a business? Use the space provided below to answer this question in five to ten sentences.
Answers
Answer:
1.Support
In most cases, the simpler the network design, the less technical support you'll require for both installation and maintenance. If you need a complex, high-speed network, consider the level of technical assistance available locally. Many small businesses can't justify the cost of full-time IT personnel. Designing a simple network that can be serviced quickly by local technicians should be a primary consideration. If your business demands a complex network beyond the capabilities of local service, design sufficient redundancy in critical network elements to ensure a minimum level of service until repairs can be made.
2.Expansion
Planning for growth in the initial stages can save future expenditures. The price difference, for example, between a 16-port switch and a 32-port switch can be negligible when compared to the cost of purchasing an new switch to replace one that is too small. Most network devices are designed to provide several years of service.
3.Outside Access
Internet access has become all but mandatory for most modern businesses. It's a good idea to consider the type of Internet connection required and the amount and type of support you will receive from your Internet service provider before designing the rest of your network. Some ISPs will provide support and advice on connection speed requirements and security concerns for commercial accounts before installation.
4.Security
Securing a network from outside intrusion or data theft is a primary concern for many companies. While it is possible to eliminate the expense of Ethernet cabling by opting for a wireless network solution, Wi-Fi networking is the least secure method of sharing data and connections. The encryption methods built into most commercial routers, Wireless Encryption Protocol (WEP), Wireless Protected Access (WPA) and the more recent WPA2, can be cracked by skilled hackers. Designing a network with hard-wired Ethernet connections eliminates the risk of intrusion to only those with physical access to the network.
5.Cost
Equipment and maintenance costs are often the first consideration in network design. Fortunately, the cost of hubs, routers and switches are relatively low when compared to the early days of networking.
Question 7 of 25 How does modularity make it easier for a programmer to fix errors in a program? A. It is easier to edit a module rather than an entire program B. It makes the errors affect the entire program C. It allows the programmer to debug an entire program instantly D. It eliminates errors altogether,
Answers
The way that modularity make it easier for a programmer to fix errors in a program is A. It is easier to edit a module rather than an entire program.
What is the modularity about?Modularity is the practice of breaking a program down into smaller, more manageable parts or modules. Each module is designed to perform a specific task, and these modules can be combined to create a larger program. By dividing a program into modules, a programmer can make the program easier to understand, maintain, and update.
One of the key benefits of modularity is that it makes it easier to fix errors in a program. When a program is broken down into modules, each module is responsible for a specific task, making it easier to isolate the source of an error.
In addition, because each module is designed to perform a specific task, it is often easier to edit a module than to edit an entire program.
Read more about modularity here:
https://brainly.com/question/11797076
#SPJ1
Answer:
A. It is easier to edit a module rather than an entire program.
Explanation:
software systems are very helpful to translators who wish to improve their technique , how?
Please
Answers
Answer:
Double-checking spelling and syntax, helping to improve and adapt their work
Explanation:
Examine trends in emergence of computer from 1936-1985 and its relevance to education industry in Nigeria
Answers
Answer:
The emergence of computers from 1936-1985 witnessed several remarkable trends that had considerable relevance to the education industry in Nigeria. Below are some of the significant trends and their relevance to the education sector in Nigeria:
1) The First Generation Computers (1936-1950s): The first computers were large, bulky, and crude devices that used vacuum tubes, magnetic drums, and punched cards for data processing. The early computers were mainly used for government and military purposes, such as code-breaking, ballistic calculations, and scientific research. The relevance of first-generation computers to the education industry in Nigeria was limited, as they were too expensive and complex for widespread adoption in schools.
2) The Second Generation Computers (1950s-1960s): In the 1950s, computers became smaller, faster, and more reliable, thanks to the invention of transistors. Second-generation computers used magnetic core memory and high-level programming languages such as COBOL and FORTRAN. These advancements made computers more accessible to businesses and government agencies, enabling them to streamline their operations and increase efficiency. However, the education industry in Nigeria still had limited access to computers due to cost and technological barriers.
3) The Third Generation Computers (1960s-1970s): The Third Generation Computers witnessed several improvements in technology, such as the development of the integrated circuit, which led to the creation of miniaturized and affordable computers. These computers were faster, more reliable, and had increased data storage capacity. They were also equipped with graphical user interfaces and interactive software, making them more user-friendly. This generation of computers became more relevant to the education industry in Nigeria, as they were affordable enough to be used in schools for teaching and learning.
4) The Fourth Generation Computers (1970s-1980s): Fourth-generation computers were faster, cheaper, and more efficient than their predecessors. The introduction of microprocessors made it possible to design computers that were small enough to fit on a desktop. This development led to the development of personal computers, which revolutionized the way people worked and communicated. Personal computers had enormous relevance to the education industry in Nigeria, as they enabled students and teachers to access information and learn new skills more easily.
In conclusion, the trends in the emergence of computers from 1936-1985 had considerable relevance to the education industry in Nigeria. Despite the technological and cost barriers that limited access to computers in the early years, the advancement of computer technology over time made it possible for computers to become an integral part of teaching and learning in Nigeria.
You open your browser and sign into the OneDrive website. Now you need to find the poster from Liam so you can make the changes Indie gave you. Which file do you need?
Answers
Type Liam's name or the name of the poster into the OneDrive search field to find the file, then open it and make the necessary adjustments as directed by Indie.
How do I access OneDrive from a web browser?Open a web browser and navigate to OneDrive.com. Choose the file name, then choose the folder where you saved your work. The proper Microsoft 365 for the Web programme launches when the document is clicked.
The best way to access files an editable link to OneDrive files be made?Choose OneDrive from the user properties page. Choose Make link to files under Gain access to files. To access the file location, select the link. Choose Move to or Copy to move the files to your computer.
To know more about OneDrive visit:-
https://brainly.com/question/17163678
#SPJ1
What is the first thing Charlotte needs to do after she opens an Excel spreadsheet?
A. Select another program
B. Select a different template
C. Select new blank program
D. Select new blank workbook
Answers
Answer: C
I hope this helps